Trying to teach myself hardware design was a monumental pain in the ass compared to learning software engineering, but today I want to tell you about 4 projects that are paving the road for anyone to go beyond telling computers what to do and to start telling them what to be!
Hardware Built For Anyone and Everyone
Let's start off with the idea that we don't want to pay a couple hundred dollars to buy an FPGA board that we have no clue how to use. The board I used to recommend was the Arty A7-35T, which has great publicly available documentation and a pretty nice set of on-board peripherals for about $150 USD. That model has been discontinued though and only the higher trim model is still available at almost double that price. I still like my Arty quite a lot but deprecated already describes way too much of my experience with logic design for FPGAs.
A couple months ago I saw the pico-ice by tinyVision.ai and... well it's an open source board with an RP2040 and an iCE40 FPGA for $35, that sounds awesome! I was thinking that the RP2040 sounded like an awesome peripheral for the FPGA... or was the FPGA the peripheral? I bet I get to choose and either way I am all for it
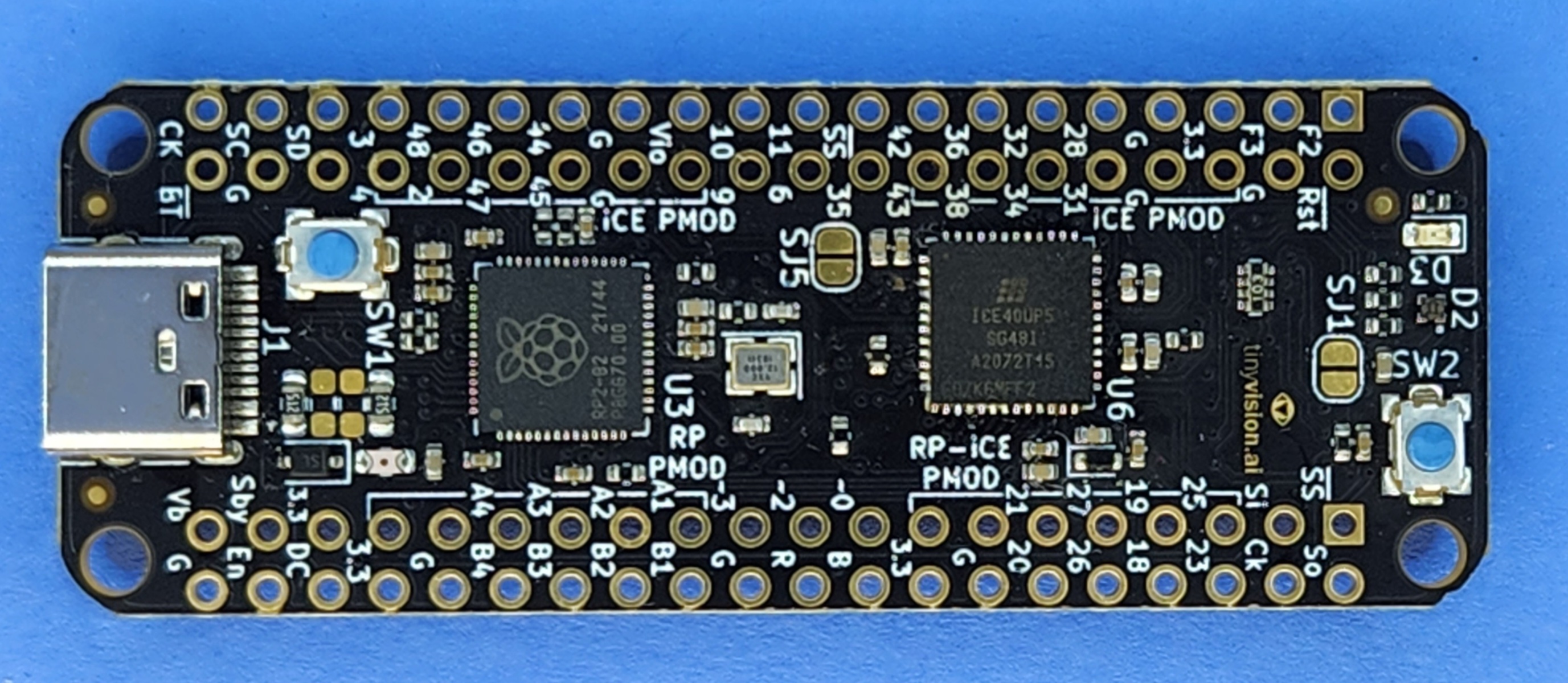
It didn't take very long to arrive, and I was excited to get started. I love the Raspbery Pi Pico but this is my first time working with a Lattice FPGA. I'm mostly familiar with Vivado so I wanted to try out the Lattice tool chain out to check it out. I downloaded and installed a few gigs of software but...
I dunno, I'm still waiting to find out
Open Source, You're my Only Hope
That was a bit disappointing, but fortunately I have other options.
oss-cad-suite is a nice binary bundle of hardware designs tools. It has HDL synthesizers, simulators and many, many other tools that are useful for logic design. It was incredibly convenient to just download and extract a directory, include it in my PATH and I'm just about ready to go.
I worked through some documentation for my pico-ice, got a little help from the tinyVision Discord and setup my project. When I finally tried to build the design I was shocked that it took literally 1 second, I assumed something must have gone wrong.
$ time fusesoc run --target pico_ice fusesoc:utils:blinky:1.1.1
INFO: Preparing fusesoc:utils:blinky:1.1.1
INFO: Setting up project
INFO: Building
INFO: Running
INFO: Running post_run script iceprog
Build was completed
To program the board run:
iceprog /tmp/blinky/build/fusesoc_utils_blinky_1.1.1/pico_ice-icestorm/fusesoc_utils_blinky_*.bin
real 0m1.030s
user 0m0.927s
sys 0m0.104s
Nothing went wrong though! I'm used to it taking minutes to synthesize even a trivial design. That's definitely something I could get used to and I'm eager to see what other goodies oss-cad-suite has in store, but I've got a couple other great projects to share.
What I was missing
My engineering nightmare is a world without package managers, and that of course leads me to FuseSoC, a tool for making your logic design experience so much better.
When I first came across FuseSoC I thought it was a high level generator focused on MCU or SoC development and I overlooked its broader capability. It's the critical tool that I was missing to enjoy logic design much more. I dabbled a bit with packaging some of my own cores and I'll be looking into making many more and trying to contribute to the project as I can.
I think FuseSoC is awesome and deserves a lot more attention and interest. The code reuse and knowledge share that can be built around this type of package manager can really help people jump into logic design when there are a lot of good building blocks to work with. We need folks of all backgrounds to mess around and share ideas. I can't wait to see what the critical mass on this looks like, it'll be absolutely amazing.
Oh, and you can make ASICs too
This to me is the most mind-explodey open source hardware project that has me excited. Through Tiny Tapeout you can make your own open source ASIC for like $100. Yes... YOU! If you're willing to try
Until this project I had pretty much assumed that for me to make an actual chip design was impossible. I'd never be able to do that... Well now I feel like I have to!
Without even installing anything you could build a small custom chip using open, browser-based schematic design tools or via HDL. I highly recommend checking it out.
My pico-ice is going to be quite busy with some prototyping!